Secure Access made Easy, Comprehensive, Flexible
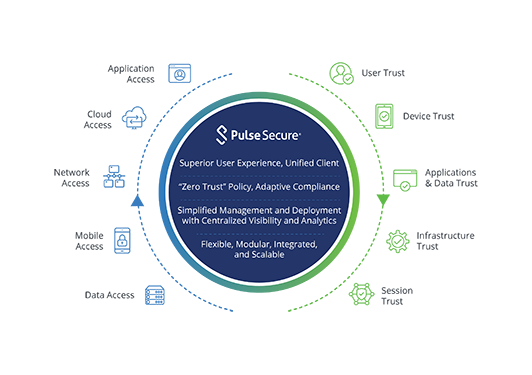
Pulse Secure’s Zero Trust framework ensures that your mobile workforce is authenticated, authorized and secure when accessing applications and resources in the data center and cloud. The user experience is simple and seamless, while administrators gain robust management, interoperability, and granular controls.
Key Features
-
Unified and Scalable Platform -
The difficulties associated with multiple security silos can be mitigated by adopting a unified Zero Trust Secure Access platform. A unified platform provides appropriate application access that supports physical and virtual IT resources across on-premise and cloud environments.
-
Unified Policy Engine for users, devices and applications -
Policy unification is another way to combat the gaps that can be created by multiple security silos. Unlike siloed solutions, policy unification enables rules to be written once and automatically applied enterprise wide.
-
Seamless integration across multiple vendors -
A unified platform and policy engine is made easier and effective by partnering with a single vendor who can orchestrate Zero Trust Secure Access controls across multiple vendor solutions.
-
Extensibility to new devices and applications -
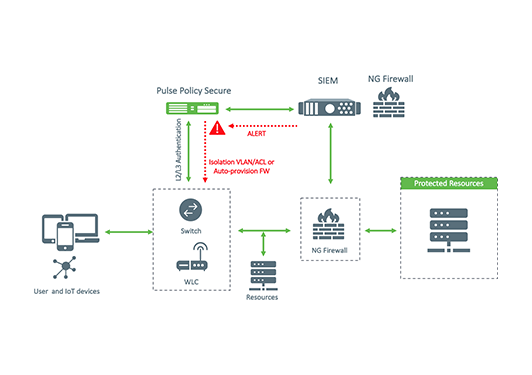
A Zero Trust Secure Access solution must be intelligent and adaptable. The solution must be able to discover, segment and monitor sanctioned and unsanctioned devices on the network and private cloud employing advanced device profiling, classification, analytics and threat response.